I love the Garmin Fenix 6 Solar, there are plenty of reviews out there that deep dive into the watch and its specs and features so I am going to focus on the watch from its travel and safety aspects and benefits.
The obvious benefit is having a GPS attached to you in case of emergency. The GPS doesn’t require cell service from your phone should you become separated from it. The battery life is great for a smart watch and I get about 20 days on a charge on average.
The big aspect for safety is a feature called Assistance. Assistance is going to be one of the few “safety apps” that I will recommend but only for a specific situation. Assistance works by having a hotkey set on the watch that when you press and hold it, will notify your emergency contact(s) that you designate in the Garmin app via SMS text that you are in trouble. When they are notified it will send them your GPS location as soon as your watch acquires the satellite connection.
This will not help you in the moment and does not substitute the need for getting training in self defense, but should for instance you get taken it will give your contact the information needed for the authorities in the area that you are traveling in start the search. It will also allow them to track you as long as you can keep the watch on you.
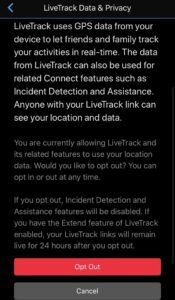
As you can probably tell this is going to require that you turn on the GPS access to your watch so that others can see it. This is called LiveTrack in the Garmin platform. Now provided you set up your phone securely which will be covered in depth at a later date, you can set this up in a relatively private manner
that I will cover at the end to mitigate and data collection that Garmin may
do, though to this point from dealings with them and their policies I have seen no evidence of data collection done in a way that releases personal information. That being said I still make it a point to anonymize my data my self as much as possible.
For this to work it does require that your phone have cell service as it needs to connect to the app to notify it to send the text message. The text message is sent from a third party number (not your own) This means that you should talk to your emergency contact ahead of time which you should be doing anyway.
Setting it up requires that you opt in to the LiveTrack. This allows Garmin to send your GPS location to your emergency contact.
You will then need input a name and city/location inside the
assistance settings in the Garmin app. As you can see from my pictures, That can be an initial and just about anything for location.
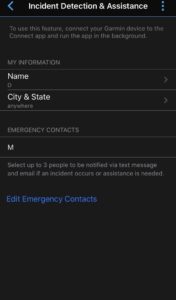
The name is used in the text message to Identify you in the message to your contact and I have not been able to pinpoint what the location input is used for.
You will then enter your emergency contacts, which can be a maximum of three who will all receive the emergency text should you press the button. As you can see you can also put as little as an initial to keep your Contacts privacy as protected as possible as well.
The picture below is an example of what the text message will look like. In this case my watch didn’t have GPS on at the time but is activated when you press the button so when the GPS is acquired it will then send follow up text with your location information. You can see the text justs says “may need help” because of this you should talk to your contacts ahead of time and decide what it means if they get the message ad what they should do.
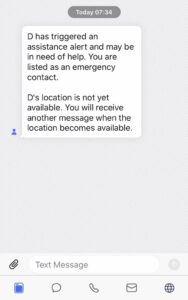
You can opt out of LiveTrack at any time and it will shut off the assistance functionality.
My set up
I always err on the side of privacy when I set up anything so I personally keep the LiveTrack functionality turned off 90 percent of time in my day to day life.
I will turn on the LiveTrack and set up the assistance each time I am headed on a trip to an area that concerns me enough that I feel the functionality is warranted. I have ahead of time let my emergency contact(s) know that I am setting them up in the app.
We then cover what it means if they get the message and what they should do. In my case I let them know that If I am going to activate the watch its most likely that I see something coming or that an incident has already happened. This is because if I don’t have time to activate the watch before something goes down I’m not going to waste time trying to activate it. I tell them they should wait 5 minutes and if I havn’t shut it off or contacted them directly to notify the authorities in the area I’m in or a specific number if I want them to contact someone specific.
Then once I am back from the trip or feel it is no longer needed I will shut off the LiveTrack access to keep any unnecessary access to my GPS location to a minimum.
Bugs
Through out my testing I ran into no bugs or miss hap with activating the assistance, the only bug I encountered early on was One time I activated it I couldn’t get it to shut off and had to re set the watch and app. Not going to be a big deal if your wanting the assistance activated.
General Review
If you are looking for a good review of the Garmin Fenix 6 Solar to look into its other features suck as activity tracking, Compass, and its other outdoor feature I personally used this review from DC Rainmaker https://www.dcrainmaker.com/2019/08/garmin-fenix6-pro-solar-series-review.html to make my decision.