A lie is a false statement made by one, to another who is entitled to hear and know the truth and which false statement tends toward injury to the other.
~JJ.lune
.
Whether to Lie or not, with only a few exceptions, is a moral issue. This means everyone has to make their own decision on when it is acceptable to lie. Of course with the few exceptions, when telling a lie is in fact illegal.
.
This applies to protecting your personal information when in person and on the internet and in this day and age your personal infosec is also your physical security.
.
Does the random person on the subway that started talking to you need to know where you were born, how old you are, where you live, or where you work?
.
Is this person just a friendly commuter looking for conversation? are they a corporate spy looking for info on a project at your work? or maybe they are a criminal deciding if you are a worthy target or not. The point is you can’t always tell a persons intentions from a single meeting
.
I am not saying lie to every one who strikes up conversation with you but take precautions and be more vague in your answers until you get to the know the person. Trust but verify.
.
JJ Luna gives an example of his personal guide lines that he follows in his book How to be invisible.
.
1. If no harm will be done, and no oath is sworn he gives false information.
2. If an oath is sworn or to be sworn he does not lie.
3. He MAY withhold or not volunteer info to government representatives unless specifically asked depending on the situation but he will not lie.
4.Under no condition whatsoever will he file a false tax return.
.
This covers most in person interactions but your infosec also applies to more passive situations where you’re not being directly interacted with but simply leave info laying around.
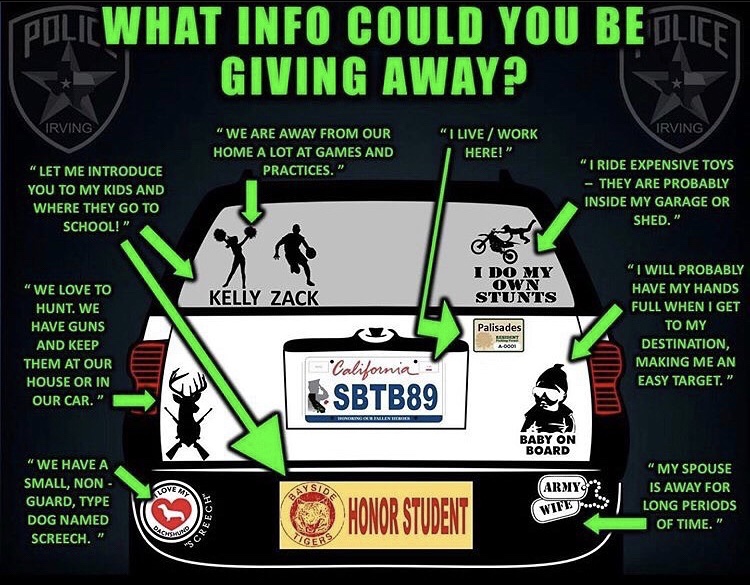
Few people realize how much information about themselves they leave lying around.
This is the bumper stickers, Parking permits on your windshield, the Stickers on your laptop, food wrappers on your floorboards, trash in garbage cans, and info on your face book (not just your profile but in your captions and comments).
.
From just a persons car you could glean where someone works or lives, where they like to eat, where their kids go to school, political affiliations just to name a few.
.
These details can all be used to decide whether or not to target you or develop a plan to target you or your family if they have already made the decision to do so.
.
Most people will say there is no reason to target me or some other form of it will never happen to me. Which statistically may be true, but if something happens and you end up on the wrong side of those stats and you haven’t taken precautions then it’s already too late.
.
You witness a crime, you cut off the wrong person in traffic, someone begins stalking you or simply being a wealthier than average individual. All are situations that the average person can find them selves in and have led to people being targeted for one crime or another. So make sure to make it as hard as possible for people to get the information about you.
If you enjoyed this post take a look at our TRUSTED RESOURCES page. If you decide to use any of the links and purchase anything we may get a small commission that helps support the site.
Sign up for our email list and you will receive exclusive content that adds to the articles we post here.